Group Behind Cisco Device Hijackings Changes Tactics to Evade
Por um escritor misterioso
Descrição
Evidence is emerging that the hacking group has updated its techniques to better conceal which Cisco devices have been hijacked.

Microsoft: How cybersecurity and AI transform threats into defenses

Attackers use dynamic code loading to bypass Google Play store's malware detections

James G. on LinkedIn: Cellebrite asks cops to keep its phone hacking tech 'hush hush

Street Cred: Increasing Trust in Passwordless Authentication

Hundreds of new cyber security simulations to keep you safe from the latest threats.

Isolation: A vaccine for template injection attacks - Blog

What is Adware? Threats Involved & How to Avoid Them
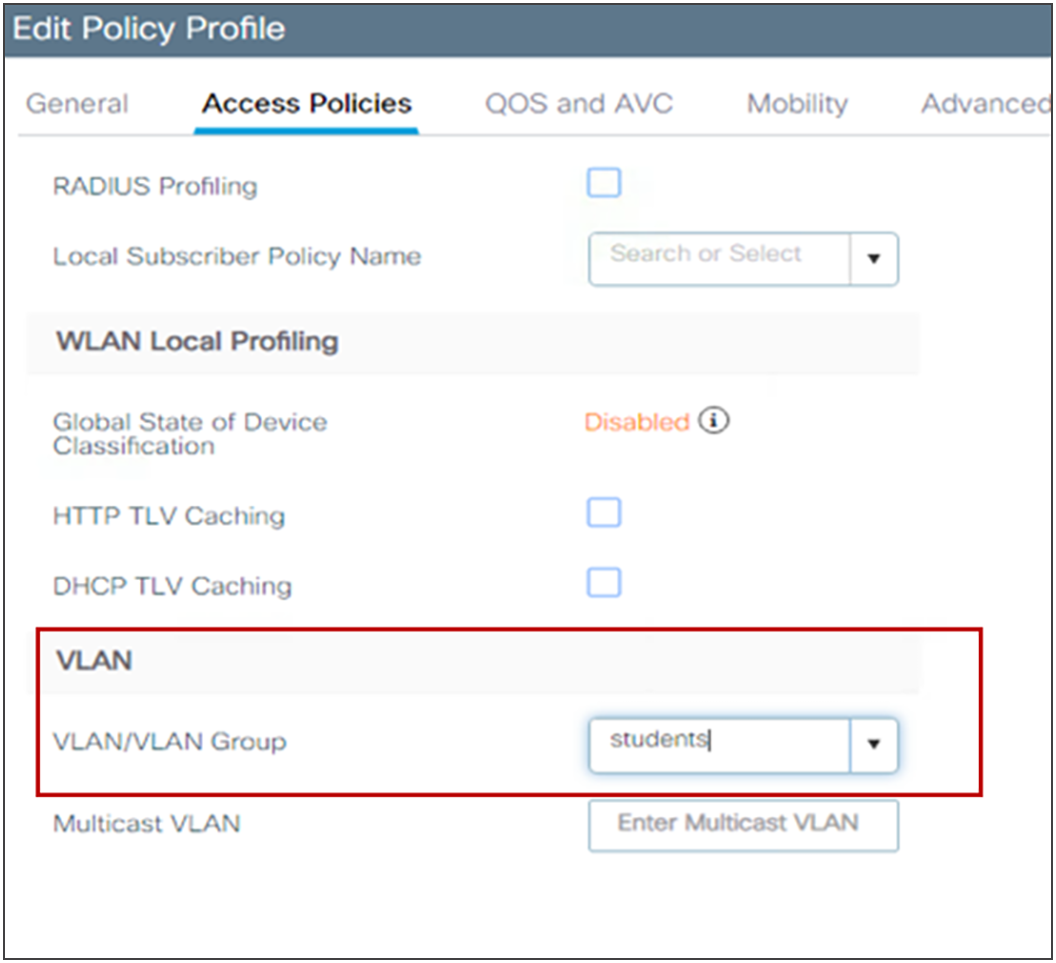
Cisco Catalyst 9800 Series Configuration Best Practices - Cisco
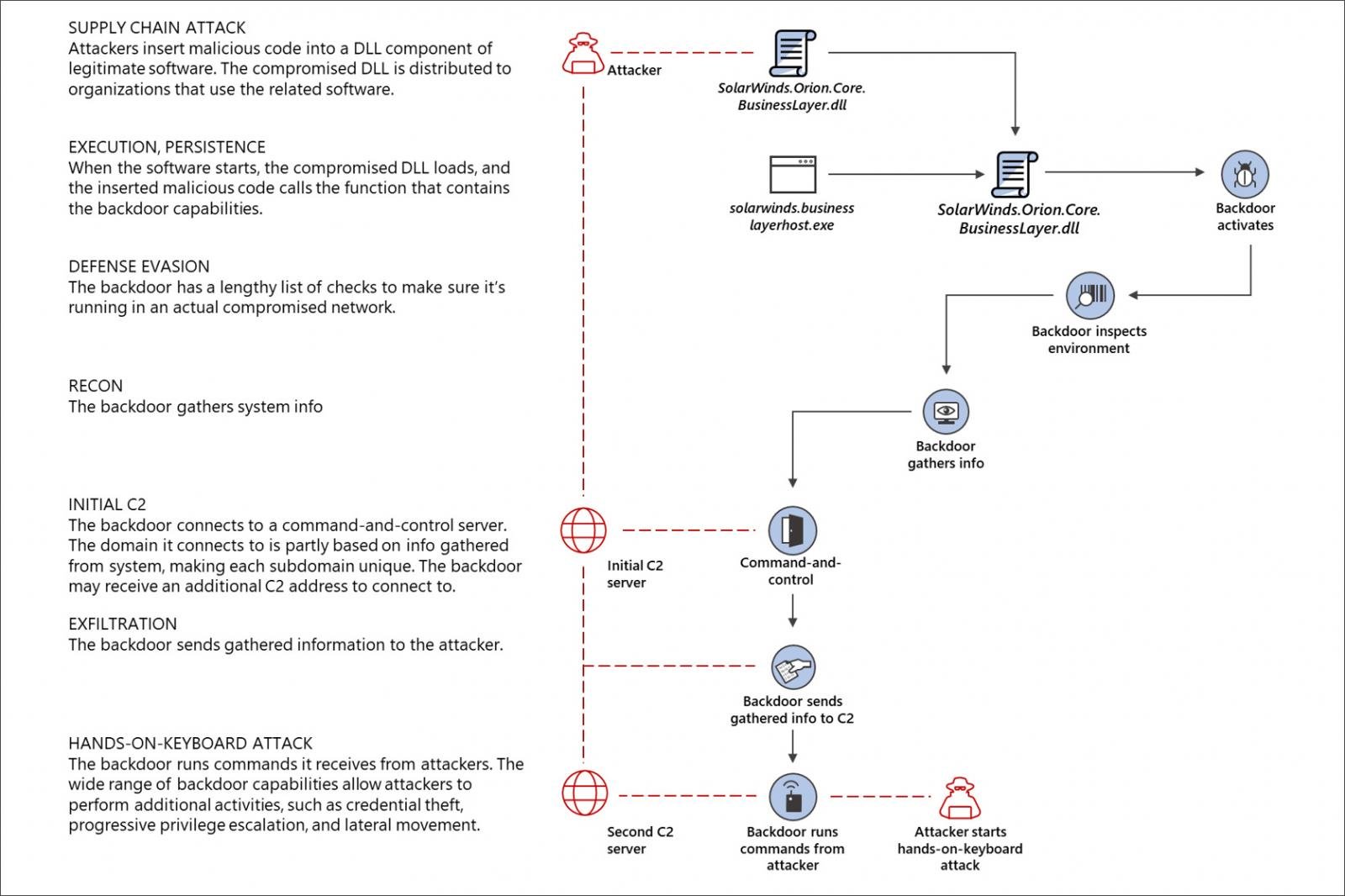
The SolarWinds cyberattack: The hack, the victims, and what we know

How a hacking group hijacks Cisco devices., James G. posted on the topic

Lazarus APT exploits Zoho ManageEngine flaw to target an Internet backbone infrastructure provider
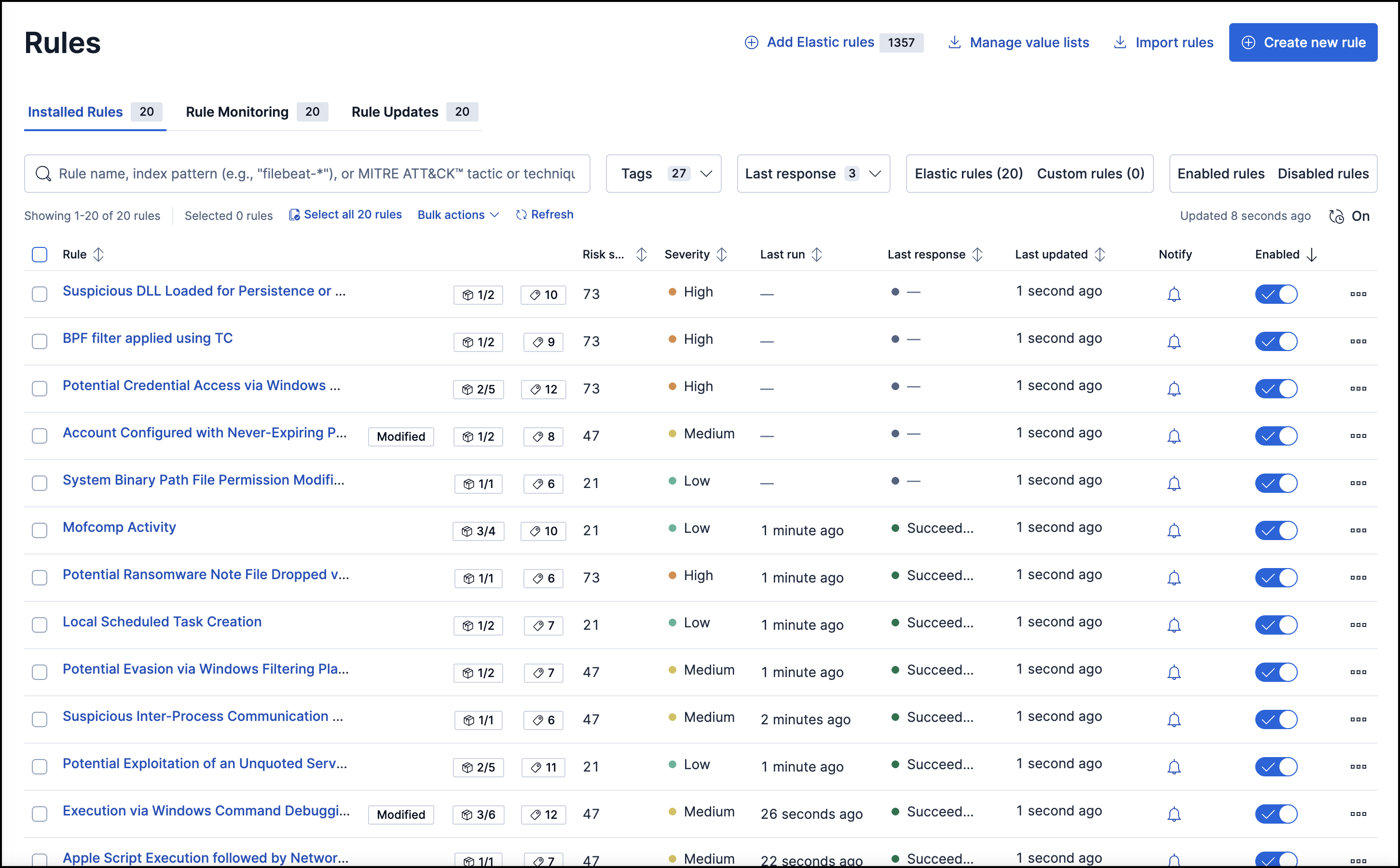
Manage detection rules, Elastic Security Solution [8.11]

VoIP Hacking: How It Works & How to Protect Your VoIP Phone

China-linked APT Volt Typhoon linked to KV-Botnet

Cisco ASA series part seven: Checkheaps, NCC Group Research Blog
de
por adulto (o preço varia de acordo com o tamanho do grupo)





:max_bytes(150000):strip_icc()/GettyImages-93453966-59684e1d3df78c57f49b0c91.jpg)