Malware analysis Suspicious activity
Por um escritor misterioso
Descrição

The General Behavior of Ransomware - Cisco Blogs
Highlight, take notes, and search in the book

Mastering Malware Analysis: A malware analyst's practical guide to combating malicious software, APT, cybercrime, and IoT attacks, 2nd Edition
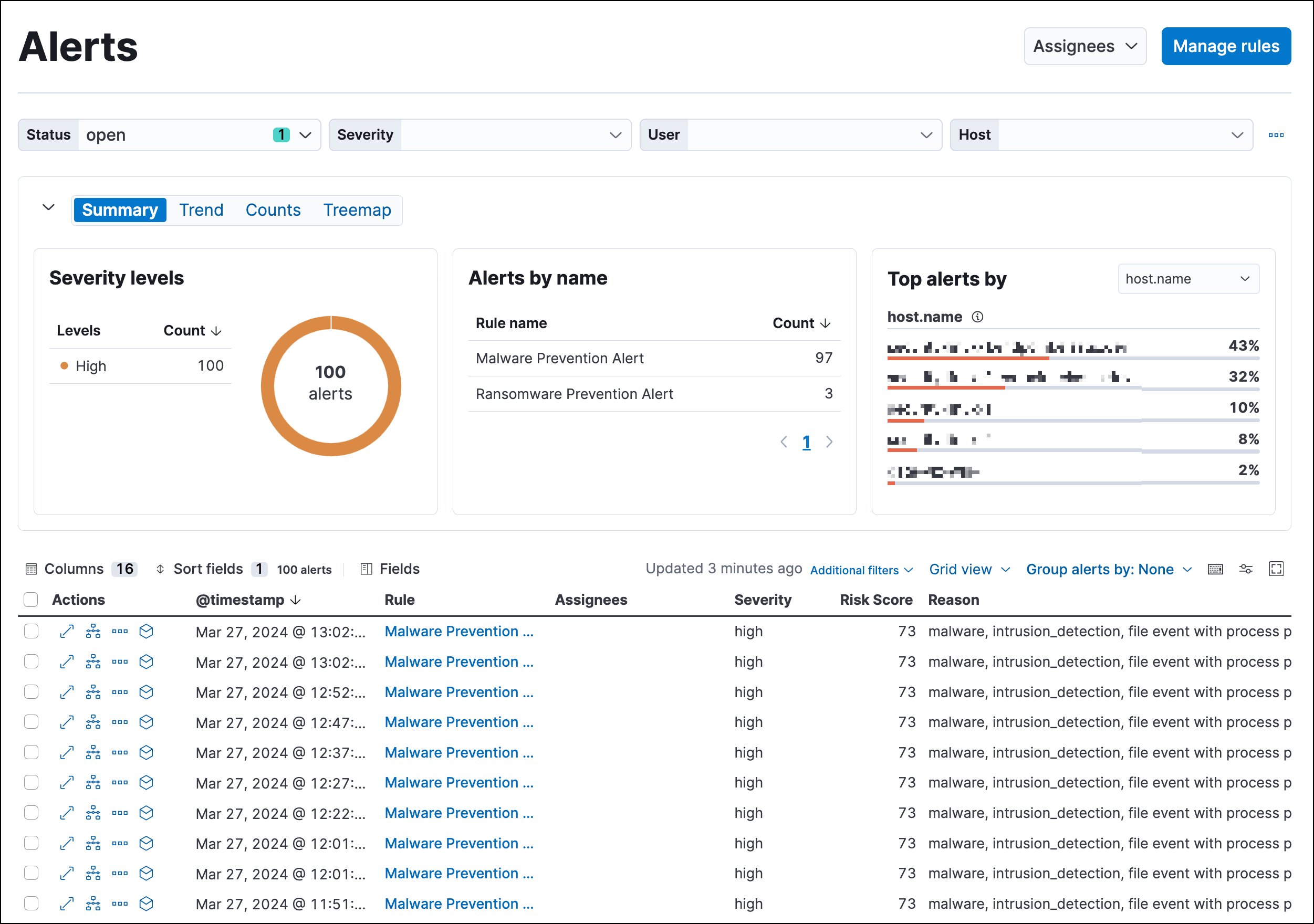
Detections and alerts, Elastic Security Solution [8.11]

How to Detect New Threats via Suspicious Activities

7 Benefits Of Dynamic Malware Analysis
How to Detect Running Malware - Intro to Incident Response Triage 2021
What is Malware Analysis? - SOC Prime
Monitoring for indicators of ransomware attacks - Splunk Lantern

Microsoft 365 Alerting - Detect and React to Threats Instantly
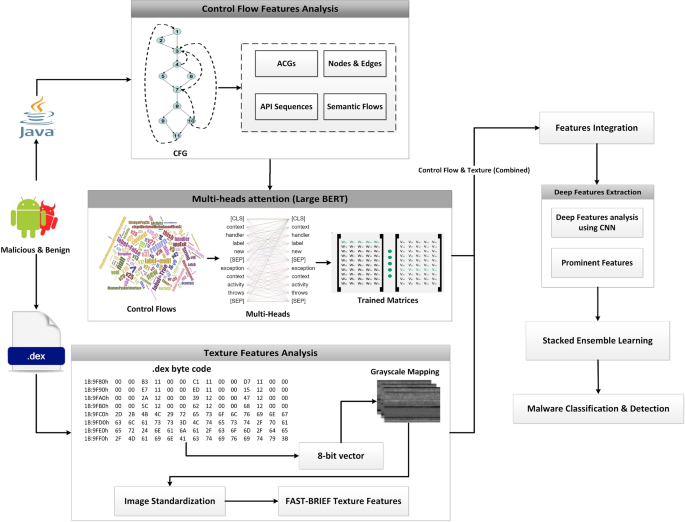
A malware detection system using a hybrid approach of multi-heads

Malware Analysis Benefits Incident Response
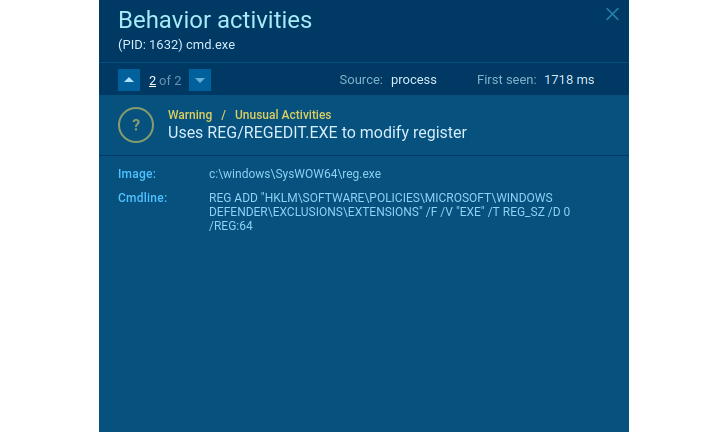
How to Detect New Threats via Suspicious Activities
11 Best Malware Analysis Tools and Their Features
de
por adulto (o preço varia de acordo com o tamanho do grupo)