Hack Like a Pro: Abusing DNS for Reconnaissance « Null Byte :: WonderHowTo
Por um escritor misterioso
Descrição

ENISA Threat Landscape Report 2016

Recon « Null Byte :: WonderHowTo

DNS hacking (beginner to advanced)

PDF) CompTIA PenTest Study Guide - Copy

DNS hacking (beginner to advanced)
GitHub - iamrajivd/pentest
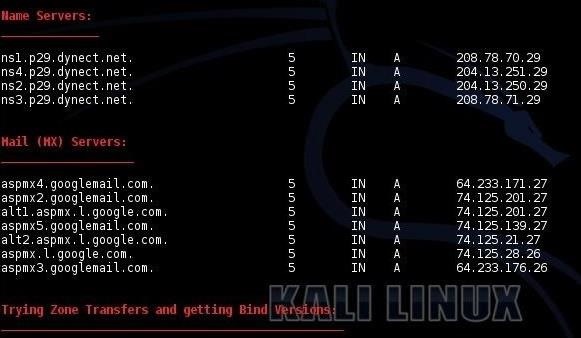
Hack Like a Pro: Abusing DNS for Reconnaissance « Null Byte

How to Uncover Hidden Subdomains to Reveal Internal Services with
What is smushing in cyber security? - Quora
GitHub - Micle5858/PENTESTING-BIBLE

TryHackMe - Passive Reconnaissance Solution - GeeksforGeeks
de
por adulto (o preço varia de acordo com o tamanho do grupo)