Threats & Research Archives - F-Secure Blog
Por um escritor misterioso
Descrição
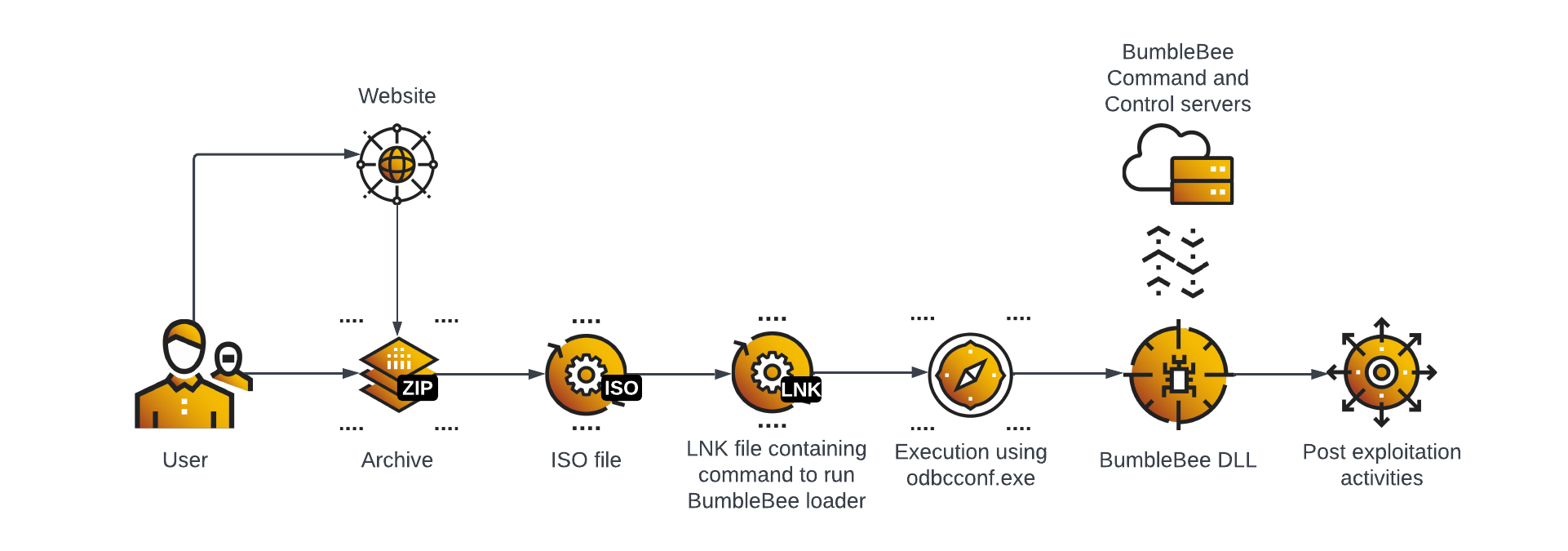
THREAT ANALYSIS REPORT: Bumblebee Loader – The High Road to

Behind the scenes of business email compromise: Using cross-domain

Threat Report Archives - F-Secure Blog

Traders' dollars in danger: CVE-2023-38831 zero-day vulnerability

Trail of Bits Blog
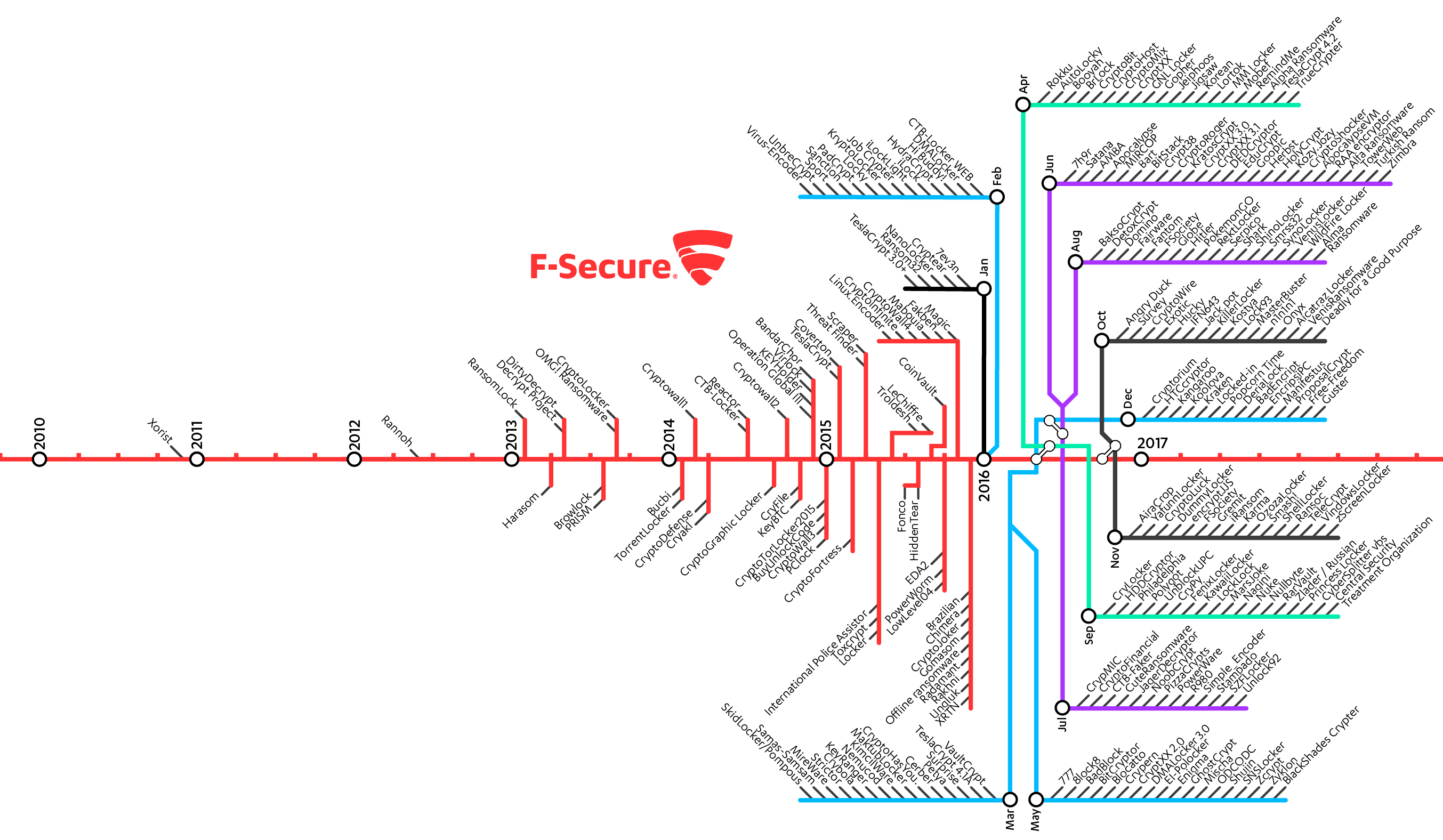
Ransomware Timeline: 2010 – 2017 - F-Secure Blog
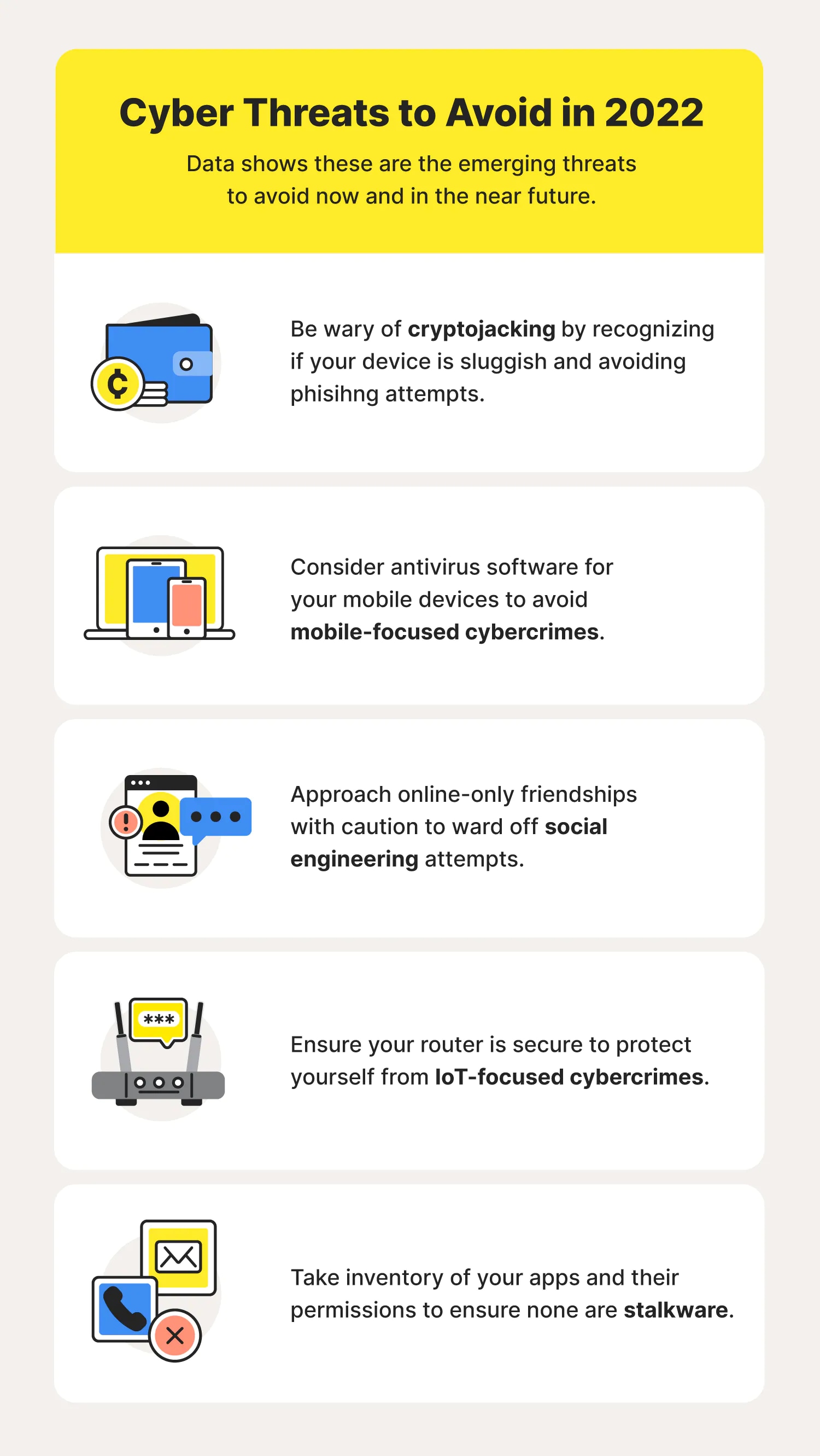
115 cybersecurity statistics + trends to know in 2024

New Threat Research: Cyberattacks by the Numbers
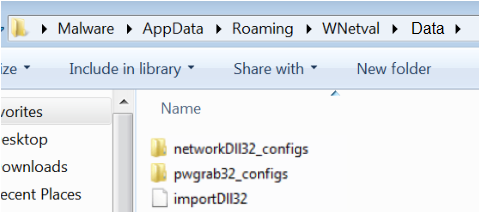
Triple Threat: Emotet Deploys TrickBot to Steal Data & Spread Ryuk

F-Secure Labs (@FSecureLabs) / X
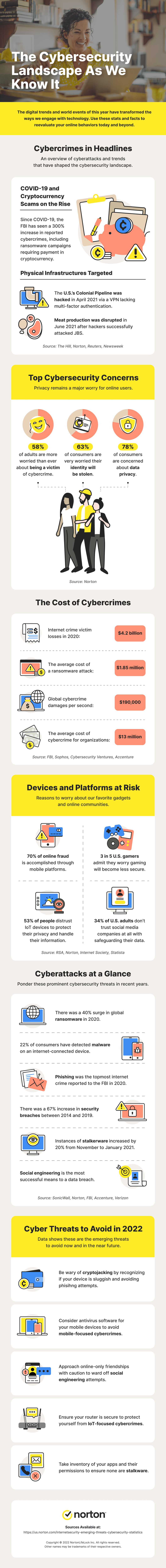
115 cybersecurity statistics + trends to know in 2024

Triaging a Malicious Docker Container – Sysdig

Antivirus software - Wikipedia
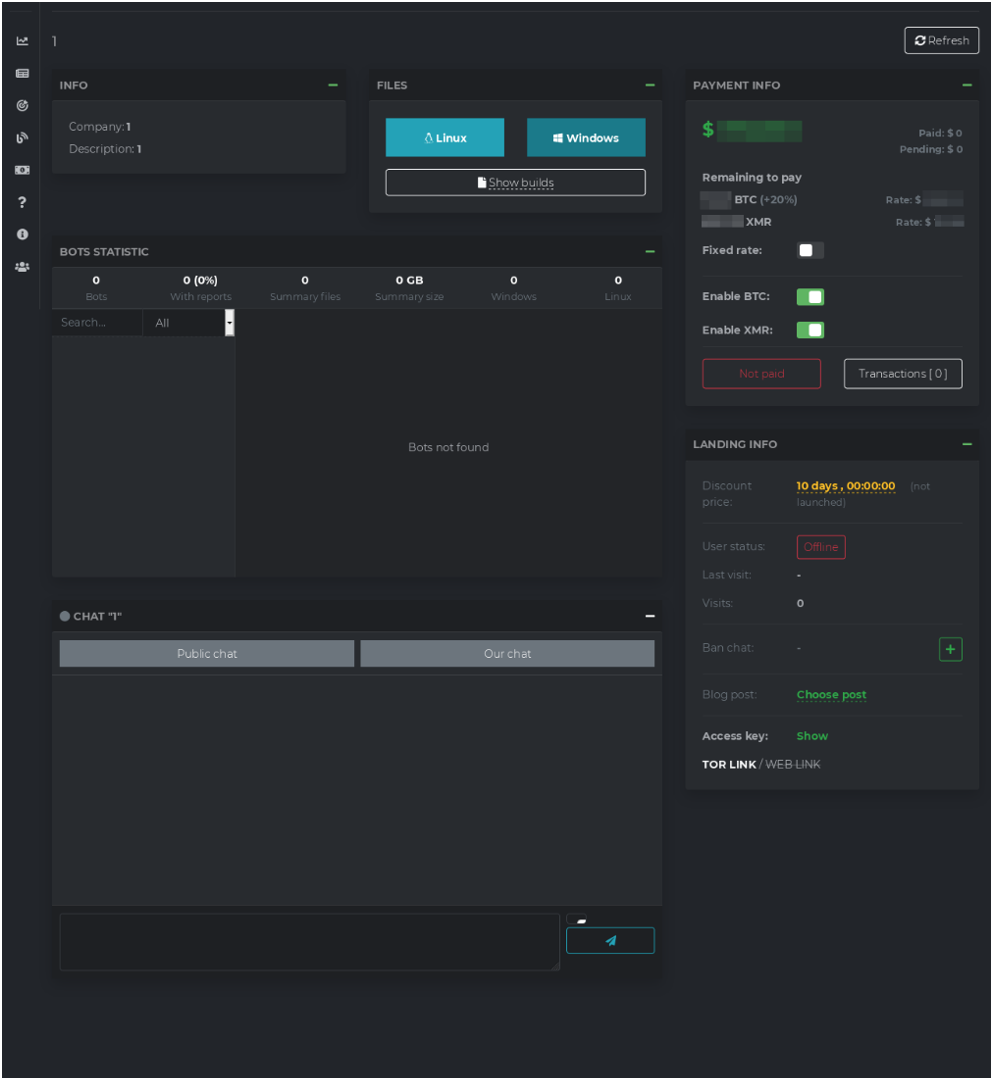
DARKSIDE Ransomware Shining a Light on Their Operations
de
por adulto (o preço varia de acordo com o tamanho do grupo)






